'WHAT' 카테고리의 다른 글
| 크롬 컴파일 (0) | 2019.03.29 |
|---|---|
| [ref] Curve cryptosystem parameters (0) | 2016.10.04 |
| pwn-pwnable [ringzer0team] (0) | 2015.06.14 |
| chal_rpc-pwnable [ringzer0team] (0) | 2015.06.11 |
| ask_grandpapa-coding [ringzer0team] (0) | 2015.06.11 |
| 크롬 컴파일 (0) | 2019.03.29 |
|---|---|
| [ref] Curve cryptosystem parameters (0) | 2016.10.04 |
| pwn-pwnable [ringzer0team] (0) | 2015.06.14 |
| chal_rpc-pwnable [ringzer0team] (0) | 2015.06.11 |
| ask_grandpapa-coding [ringzer0team] (0) | 2015.06.11 |
https://en.wikipedia.org/wiki/Google_Chrome_version_history
chrome github commit + chrome v8 engine version
git clone https://chromium.googlesource.com/chromium/tools/depot_tools.git
export PATH=$PATH:/path/to/depot_toolshttps://v8.dev/docs/source-code
mkdir ~/v8
cd ~/v8
fetch v8
cd v8
git checkout -b 1a1a1a1a1a
* 1a1a1a1a1a 는 크로미움의 버전이 아니라 v8의 커밋 버전임(주의)
* 크로미움 버전 : 63.0.3239
* (Linux, macOS, and Windows) Blink 537.36
* v8 버전 : 6.3.292cd ~/v8/v8 && ./build/install-build-deps.sh
gclient synctools/dev/v8gen.py list
tools/dev/v8gen.py ia32.releaseninja -C out/x64.release : 전체 빌드 약 1300개
ninja -C out/x64.release d8 : d8만 빌드 약 900개, 대략 1시간 소요
[참조]
root@0df6d19cd3c1:/hack/v8/v8# tools/dev/v8gen.py x64.debug
root@0df6d19cd3c1:/hack/v8/v8# ninja -C out.gn/x64.debug
ninja: Entering directory `out.gn/x64.debug'
[15/1390] CXX obj/simple_fuzzer/fuzzer.o^C
ninja: build stopped: interrupted by user.
root@0df6d19cd3c1:/hack/v8/v8# ninja -C out.gn/x64.debug d8
ninja: Entering directory `out.gn/x64.debug'
[21/966] CXX obj/v8_libplatform/trace-config.o| vmware tool 수동 설치 ubuntu server 18.04 (0) | 2019.03.29 |
|---|---|
| [ref] Curve cryptosystem parameters (0) | 2016.10.04 |
| pwn-pwnable [ringzer0team] (0) | 2015.06.14 |
| chal_rpc-pwnable [ringzer0team] (0) | 2015.06.11 |
| ask_grandpapa-coding [ringzer0team] (0) | 2015.06.11 |
http://www.johannes-bauer.com/compsci/ecc/ 에서 발췌
In order to turn all these mathematical basics into a cryptosystem, some parameters have to be defined that are sufficient to do meaningful operations. There are 6 distinct values for the Fp case and they comprise the so-called "domain parameters":
Generating a keypair for ECC is trivial. To get the private key, choose a random integer dA, so that
Then getting the accompanying public key QA is equally trivial, you just have to use scalar point multiplication of the private key with the generator point G:
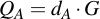
Note that the public and private key are not equally exchangeable (like in RSA, where both are integers): the private key dA is a integer, but the public key QA is a point on the curve.
| vmware tool 수동 설치 ubuntu server 18.04 (0) | 2019.03.29 |
|---|---|
| 크롬 컴파일 (0) | 2019.03.29 |
| pwn-pwnable [ringzer0team] (0) | 2015.06.14 |
| chal_rpc-pwnable [ringzer0team] (0) | 2015.06.11 |
| ask_grandpapa-coding [ringzer0team] (0) | 2015.06.11 |